What would happen if one of your vendors suffered a breach today?
Would your data be exposed? Would operations grind to a halt? For many companies, the answer is yes—and the risk is widespread.
In fact, according to Adler (n.d.), 98% of organizations work with at least one third-party vendor that has experienced a data breach.This reality highlights the importance of identifying critical vendors, those that support essential services, process sensitive data, or have access to your internal systems. Without clear visibility into who your most vital vendors are, your organization may be blindsided by avoidable threats. In this article, we’ll walk through a structured, risk-based approach to pinpointing your critical vendors and protecting your business from cascading third-party risks.
What Is a Critical Vendor?
A critical vendor is any third-party provider whose failure or compromise would cause a significant disruption to your organization. These vendors support essential business operations, access or process sensitive data, or are tied to regulatory compliance obligations. While many vendors are valuable, only a subset rises to the level of “critical.”
Definition and Role in Your Organization
A critical vendor can fall into one or more of these categories:
- Operates infrastructure or services core to your daily operations (e.g., cloud providers, data centers)
- Has access to internal systems or privileged credentials
- Handles regulated or sensitive information such as PII, PHI, or financial records
- Cannot be easily replaced or substituted
- Is required by law or regulation to be monitored or assessed
Key Differences: Critical vs. Non-Critical Vendors
| Criteria | Critical Vendor | Non-Critical Vendor |
| Business Dependency | High – operations may halt if disrupted | Low – operations can continue |
| Data Sensitivity | Handles sensitive/regulated data | Minimal or no access to sensitive data |
| System Access | Direct access to internal or production systems | No system or limited access |
| Regulatory Relevance | Often subject to specific oversight | Generally low or no regulatory impact |
| Vendor Substitutability | Hard to replace or time-consuming | Can be replaced with minimal effort |
Regulatory Lens: NIS2, DORA, FFIEC
Several regulations and frameworks define or emphasize the need to assess and monitor critical vendors:
| Regulation | Mentions of Critical Vendors | Key Requirements |
| NIS2 | Yes | Requires identifying suppliers essential to service delivery and security |
| DORA | Yes | Focuses on oversight of ICT third-party providers deemed critical to operations |
| FFIEC | Yes | Highlights the need to identify and manage third parties that pose material risk |
| HIPAA | Indirect | Requires diligence for third parties handling protected health information (PHI) |
Why It’s Important to Identify Critical Vendors Early
Failing to recognize your critical vendors can leave your organization exposed to serious consequences—from operational disruption to regulatory penalties. Early identification allows you to prioritize risk management efforts where they matter most.
Cybersecurity Impact
Third-party vendors are increasingly exploited by attackers looking for indirect access to target systems. High-profile incidents like the Fortra GoAnywhere breach (2023) and the Change Healthcare ransomware attack (2024) show how a single compromised vendor can disrupt critical services and ripple across entire industries.
Key risks include:
- Unauthorized data access through trusted vendor connections
- Ransomware infiltration via vendor tools or software updates
- Loss of visibility into vendor-level security controls
A proactive approach to identifying critical vendors gives you the ability to apply tighter controls and implement continuous monitoring where the stakes are highest.
Operational and Business Continuity Risk
When a critical vendor fails—due to cyberattack, financial collapse, or service degradation—your ability to operate can be severely affected. Consider:
- A cloud provider outage causing app downtime
- A payroll vendor breach delaying employee payments
- A communications platform disruption interrupting customer service
Having identified critical vendors allows you to build contingency plans, diversify dependencies, and respond faster when incidents occur.
Compliance and Regulatory Pressure
Many data protection and sector-specific regulations require organizations to evaluate and manage third-party risk. Failing to properly identify and assess critical vendors can result in:
- Regulatory fines
- Lawsuits or class actions
- Breach of contract issues with clients or partners
By classifying vendors based on criticality, you can align due diligence and oversight efforts with compliance expectations such as NIS2, DORA, FFIEC, or GDPR.
Common Characteristics of a Critical Vendor
Identifying critical vendors requires understanding the specific attributes that elevate a vendor’s importance to your organization’s operations and security. Here are key characteristics to consider:
1. Access to Sensitive Data or Systems
Vendors that handle or have access to sensitive information or critical systems are inherently higher risk. This includes:
- Personal Identifiable Information (PII): Names, Social Security numbers, addresses.
- Protected Health Information (PHI): Medical records, health insurance details.
- Financial Data: Credit card numbers, bank account information.
- Intellectual Property: Proprietary business information, trade secrets.
2. Direct Support for Core Business Functions
Vendors integral to your primary business operations are critical. Examples include:
- Cloud Service Providers: Hosting essential applications and data.
- Payment Processors: Handling transaction processing.
- IT Support Services: Managing network infrastructure and support.
3. Regulatory or Legal Obligations
Some vendors are critical due to compliance requirements. For instance:
- Healthcare Vendors: Subject to HIPAA regulations.
- Financial Services Vendors: Must comply with SOX, GLBA, or PCI DSS standards.
4. High Financial or Operational Impact if Compromised
Assess the potential impact of a vendor’s failure or breach:
- Operational Downtime: Can the business function without this vendor?
- Financial Losses: Potential costs associated with a breach or service disruption.
- Reputational Damage: Public perception following a vendor-related incident.
5. Involvement in High-Risk Processes
Vendors engaged in processes that are inherently risky require closer scrutiny:
- Data Analytics Firms: Processing large volumes of sensitive data.
- Third-Party Marketing Agencies: Accessing customer information for campaigns.
Outsourced Customer Service Centers: Handling customer interactions and data.
How to Identify a Critical Vendor: Step-by-Step Process
Identifying critical vendors doesn’t have to be guesswork. By using a structured approach, organizations can uncover which third parties pose the highest risk and require prioritized oversight.
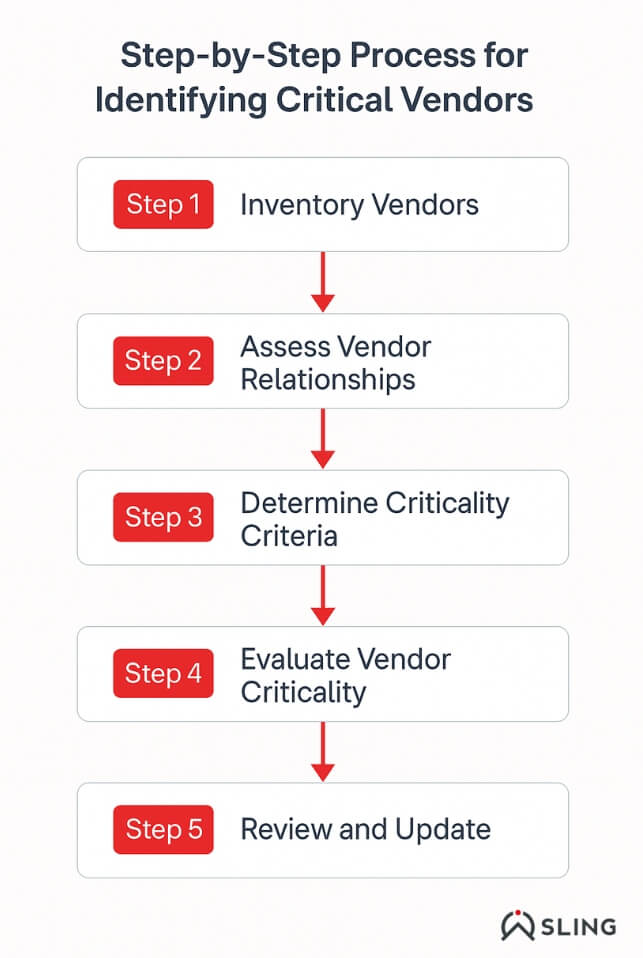
Step 1 – Inventory All Vendors
Start by creating a centralized and complete vendor inventory.
- Include all third parties with access to systems, data, or internal processes.
- Don’t forget shadow IT—tools or services adopted without formal IT approval.
- Collaborate with procurement, IT, and business units to capture a full picture.
Step 2 – Map Vendors to Business Services
Connect each vendor to the business function they support.
- Is the vendor tied to a core operation (e.g., payroll, infrastructure, identity management)?
- What internal teams rely on the vendor’s services to function daily?
- Use this mapping to assess the business dependency of each vendor.
Step 3 – Evaluate Risk Criteria
Rate each vendor based on objective risk criteria. Common factors include:
- Type of data accessed or processed
- Level of system access (e.g., admin, read-only)
- Regulatory exposure (e.g., handling PHI or PCI data)
- Availability impact if the vendor is offline or compromised
- Reputational or legal consequences if the vendor is breached
Step 4 – Collaborate with Stakeholders
Involve key business owners in the process.
- Department heads can validate a vendor’s importance and risk level.
- Legal and compliance teams can flag regulatory exposure.
- IT can assess technical dependencies and access levels.
Cross-functional input ensures the assessment reflects both business and security perspectives.
Step 5 – Categorize Vendors by Tier
Once vendors are assessed, segment them by criticality:
| Vendor Name | Data Access | System Dependency | Regulatory Exposure | Tier |
| AWS | High | High | Yes | 1 (Critical) |
| Payroll Service | High | Medium | Yes | 1 (Critical) |
| Email Marketing Tool | Medium | Low | No | 3 (Low Risk) |
Tier 1 vendors are critical and require the most oversight, while Tier 2 and Tier 3 vendors may need lighter monitoring or periodic reviews.
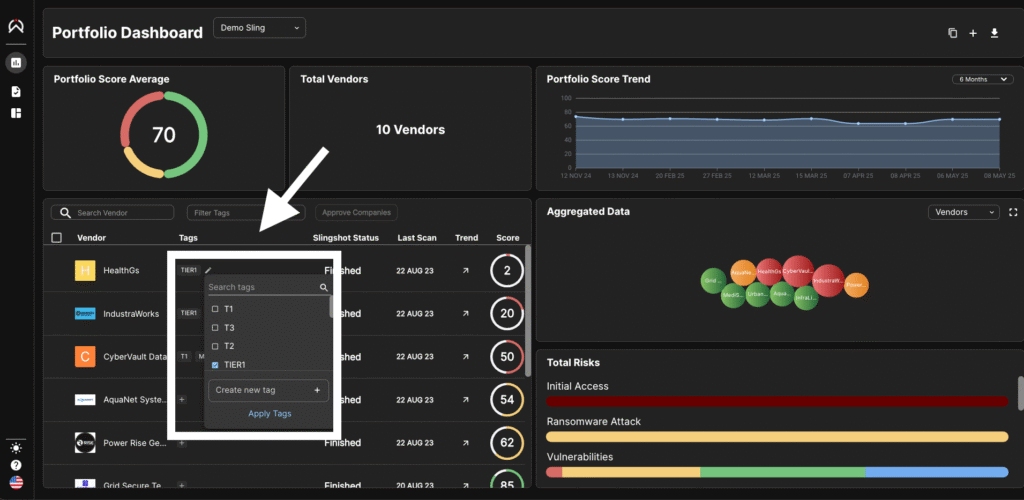
Sling gives users the flexibility to assign vendor tiers based on their own internal criteria, such as data sensitivity, regulatory relevance, and operational dependency. This tiering capability helps organizations clearly prioritize which vendors require deeper scrutiny, and stronger controls.
Tools and Frameworks for Identifying Critical Vendors
Identifying critical vendors manually can be time-consuming and inconsistent across departments. Fortunately, some tools and frameworks help streamline and standardize the process—allowing for more confident and data-driven decisions.
1. Risk Assessment Questionnaires
Structured questionnaires are a foundational tool for evaluating third-party risk. These typically assess:
- Data types handled by the vendor
- Security and privacy controls in place
- Incident response capabilities
- Compliance with standards like SEC, ISO 27001, or HIPAA
Common templates include:
- SIG (Standardized Information Gathering Questionnaire) by Shared Assessments
- CAIQ (Consensus Assessments Initiative Questionnaire) from the Cloud Security Alliance
- Custom internal forms tailored to your risk appetite
Questionnaires are especially useful in onboarding and annual reassessments of vendors.
2. Cyber Risk Ratings Tools
These tools provide external, objective insights into a vendor’s security posture using signals such as:
- Domain hygiene
- Network vulnerabilities
- History of breaches or incidents
- Patch cadence and endpoint protections
3. Internal Risk Scoring Models
Developing your own weighted scoring system can align vendor classification with your organization’s unique priorities.
A typical scoring model may consider:
| Risk Factor | Weight (%) | Vendor A Score |
| Data Sensitivity | 30% | High |
| System Access | 25% | Medium |
| Compliance Requirements | 20% | High |
| Financial/Operational Impact | 25% | High |
Vendors scoring above a certain threshold (e.g., 75%) may be flagged as Tier 1 – Critical.
4. TPRM Platforms Like Sling
Tools like Sling simplify the process by allowing users to:
- Centralize vendor data and documentation
- Assign tier levels manually
- Track cyber posture and breach intelligence in real time
- Automate risk tracking, reminders, and reassessments
- Generate reports to meet regulatory expectations
Using a dedicated TPRM platform ensures consistency across teams, improves visibility, and reduces the overhead of managing third-party risk manually.
Managing Critical Vendors After Identification
Once a vendor is classified as critical, it must be managed with heightened oversight and controls.
Key Practices:
- Enhanced Due Diligence
Request detailed documentation like SOC 2 reports, incident response plans, and compliance certifications. - Ongoing Monitoring
Use cyber risk tools or platforms like Sling to continuously track risk signals, breach alerts, and security posture changes. - Contingency Planning
Maintain clear offboarding procedures, alternative providers, and strong SLAs to ensure operational continuity if the vendor fails.
Effectively managing critical vendors reduces the likelihood of disruptions and ensures compliance with security and regulatory requirements.
Real-World Example: Identifying a Critical Vendor
Let’s consider a real-world scenario that illustrates how identifying a critical vendor can strengthen resilience and prevent major disruption.
Scenario: Cloud Infrastructure Dependency
A mid-sized fintech company relies on a cloud service provider (CSP) for hosting its customer-facing application and managing sensitive financial data. During a routine vendor review, the risk team identifies the CSP as:
- Having direct access to production systems
- Storing customer PII and payment data
- Playing a central role in service availability
Action Taken:
- The CSP was classified as a Tier 1 Critical Vendor in the company’s risk register.
- Enhanced due diligence was conducted, including review of SOC 2 and ISO 27001 certifications.
- A business continuity plan was created, including backups with an alternate cloud provider.
- Ongoing risk monitoring was enabled via a cyber risk intelligence platform.
Outcome:
When the CSP experienced a regional outage months later, the company was able to fail over to its backup provider within hours—avoiding downtime, reputational damage, and customer churn.
Final Thoughts on Identifying Critical Vendors
In third-party risk management, not all vendors carry the same weight. A small subset—critical vendors—play a central role in keeping the business running securely and efficiently. If one of them fails or is compromised, the impact can be immediate and far-reaching.
That’s why identifying critical vendors early is so important.
By asking the right questions—Which vendors support essential services? Who has access to sensitive data?—organizations can focus their security and compliance efforts where they’re most needed.
With the right process and tools in place, teams can evaluate risk consistently, assign tiers thoughtfully, and respond proactively to emerging threats. Platforms like Sling support this effort by helping organizations track vendor exposure, assign criticality levels, and streamline ongoing oversight.
Ultimately, identifying and managing critical vendors isn’t just a compliance exercise. It’s a strategic move that strengthens operational resilience and protects the business from the ground up.